Threat Report: Ransomware Targets CyberAlberta Community of Interest Member
TLP:CLEAR
Source: Closed Source | CyberAlberta Investigation
Overview
CyberAlberta recently became aware of a major incident where an affiliate of a prolific ransomware operation (henceforth referred to as the ‘threat actor’) had launched an attack on an CyberAlberta Community of Interest member organization. The attack had successfully compromised the organizations network defenses, spreading to multiple platforms, including VMWare ESXi and Microsoft systems. This attack resulted in the encryption of sensitive data, causing loss of access to several critical systems, which forced the organization to resort to manual means of conducting business, and lengthy periods of network downtime.
The threat actor was able to perform the majority of the observed activity relying on tools that are native to the Windows operating system, as well as commercially available legitimate products. The incident response and investigative efforts have revealed insight into the threat actors TTPs, and their infrastructure. Readers are encouraged to consider the recommendations offered in this report to mitigate the malicious usage of native and legitimate tools.
Note: This report was made possible thanks to the collaborative incident response efforts of ISA Cybersecurity and others.
Technical Details
Initial Access
Post-incident investigation had revealed evidence of potential phishing attacks targeting Microsoft 365 accounts; however, the exact method of initial access remains unconfirmed at this stage. Following initial access, brute-force attacks were observed from a locally authenticated user on subsequent servers. Brute-force attacks involve rapidly attempting to authenticate into additional accounts using a pre-determined list of credentials. Accounts not protected by either strong password policies or multi-factor authentication (MFA) are particularly vulnerable to this attack.
Execution
The threat actor had used PsExec (PSEXEC.exe) to attempt remote execution of processes across the network. PsExec is a legitimate, free tool that is part of the Microsoft SysInternals suite used to perform administrative tasks on networks.
Persistence and Privilege Escalation
By deploying custom batch scripts on to compromised systems, the threat actor was able to perform the following:
- net commands to create local accounts and add them to administrator groups.
- reg commands to interact with the Registry, enabling connections over the Remote Desktop Protocol (RDP) service.
- netsh commands to allow RDP traffic over 3389 inbound to the victim's firewall.
These commands granted the threat actor with administrator privilege accounts on multiple devices, which were used to enable the RDP service to facilitate communication across endpoints and to external threat actor-controlled infrastructure.
Credential Access
Post-incident investigation discovered evidence of the use of Task Manager (tskmgr.exe) and Ntdsutil (Ntdsutil.exe) to extract credential. Furthermore, a ZIP folder named lsass.zip was stored on several servers, including compromised domain controllers (DCs).
- Task Manager can be used to create a memory dump of the LSASS process, which attackers can exfiltrate to crack offline, granting access to the credential data held within such as plaintext credentials, NTLM hashes, and Kerberos tickets.
- Ntdsutil is a native tool used for administrating Active Directory (AD) and can be used to create a backup of the NTDS.dit file, which contains hashed credentials that can also be exfiltrated and cracked offline.
Living-off-the-Land Techniques (LotL)
Threat actors using native tools such as PsExec, Task Manager, or Ntdsutil to perform steps of their attack is referred to as Living-off-the-Land (LotL). These techniques enable threat actors to avoid detection by security products, as well as reducing the requirement for threat actors to develop and install custom malware onto target devices. Using LotL techniques, which are now commonplace in the cybersecurity landscape, malicious activity can blend in with routine operations, making it harder to detect and investigate. To meet this challenge, security teams are required to perform behavioral analysis and to have an in-depth awareness of baseline activity in networks to identify threats.
Discovery
The threat actor used the SoftPerfect Network Scanner (netscan.exe) to perform reconnaissance for services that were running on the target network. By doing so, the threat actor may have been able to identify further available points of access to spread throughout the network. SoftPerfect Network Scanner is another legitimate and commercially available tool frequently abused by threat actors for its ability to map out network connections.
Lateral Movement
The threat actor had used a compromised domain admin account to authenticate to other systems and run the previously mentioned batch scripts to create new malicious admin accounts and enable RDP. Furthermore, Pass-the-Hash (PtH) attacks were also performed using previously stolen credential data, granting access from a compromised DC to other endpoints on the network.
Command and Control (C2)
To create a C2 channel, the threat actor deployed MeshCentral onto a compromised DC and used ngrok to establish a reverse proxy tunnel between the compromised DC, and the threat actor's infrastructure. Furthermore, the threat actor enabled an RDP connection over the ngrok tunnel, effectively giving them full graphical and interactive control of the compromised devices. MeshCentral, ngrok, and RDP are all legitimate services frequently abused by threat actors due to their lower likelihood of detection by security products in target organizations.
- MeshCentral is a free and open-source remote monitoring and management (RMM) tool which enables the ability to perform tasks on a connected device remotely. Other legitimate tools with RMM capabilities such as Atera, AnyDesk, TeamViewer, and SimpleHelp are also frequently abused by threat actors in a similar way.
- ngrok is commonly used by threat actors to establish a reverse proxy connection to threat actor-controlled infrastructure. In this incident, as in many others involving this tool, the network tunnel created by ngrok allowed threat actors to connect previously isolated compromised devices to the internet, bypass firewall restrictions, and exfiltrate data.
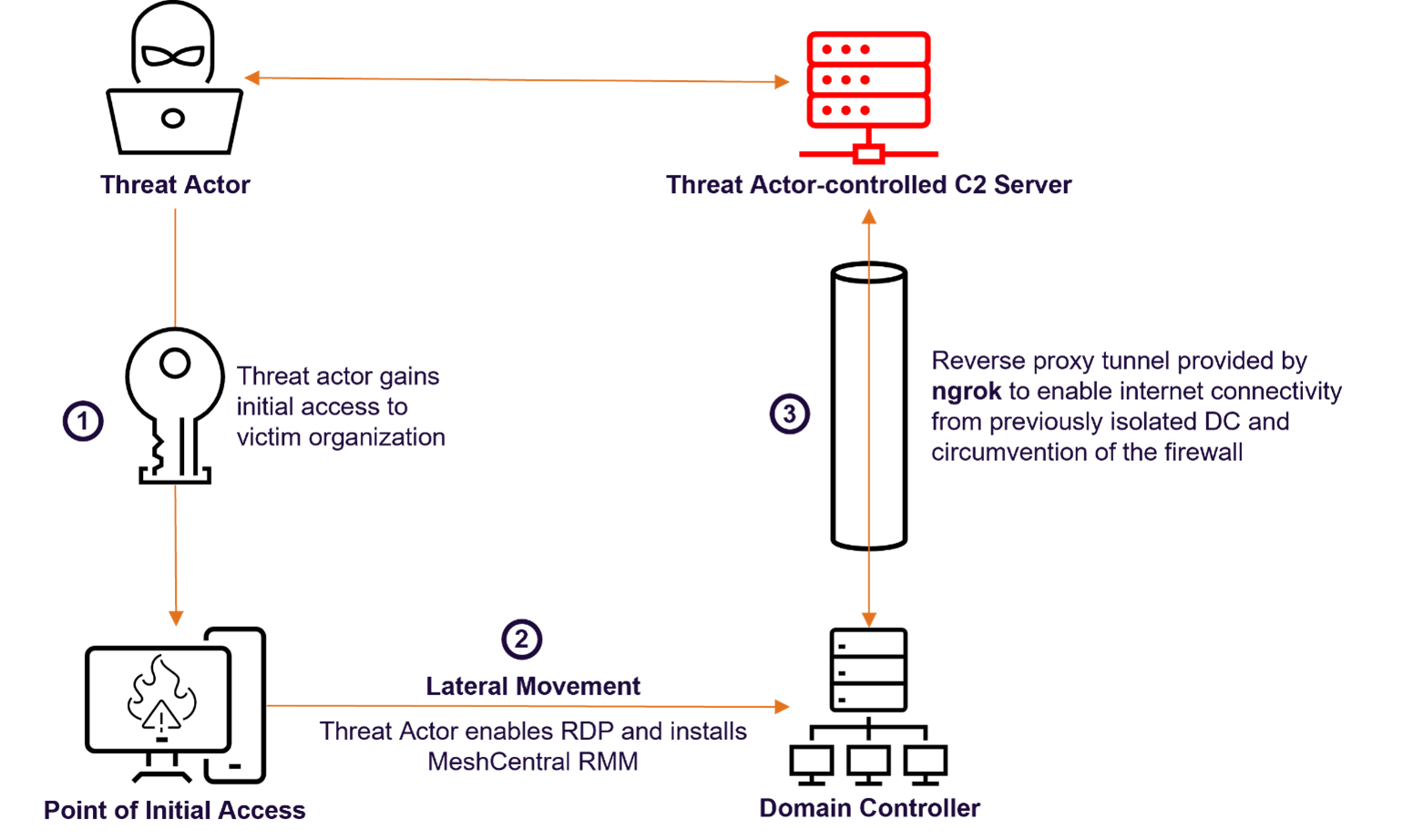
Figure 1 - Flow diagram illustrating the steps in the attack that led to the establishment of a reverse proxy tunnel from a domain controller to the threat actor's C2 server.
Defense Evasion
Further to the previously mentioned defense evasion techniques such as LotL and the use of legitimate tools, the threat actor also renamed the MeshCentral agent to msedge.exe to masquerade as the legitimate Microsoft Edge browser.
Impact
This attack had resulted in data held on network shares being encrypted, severely disrupting business operations. The affected organization had to resort to conducting operations using manual alternatives to their IT solutions, as well as implementing network containment for over two weeks, resulting in the loss of access to services for their area of responsibility.
Recommendations
The actions observed by the threat actor in this attack, particularly the use of LotL techniques are common among ransomware attacks today. To help mitigate these attack techniques, please consider adopting the recommendations provided below, if not done so already.
- Enable detection of processes that:
- Add anomalous accounts to administrator groups.
- Modify the Registry on a device to enable the RDP service.
- Create firewall rules to permit inbound RDP connections (over port 3389).
- Implement monitoring for anomalous outbound RDP traffic.
- Enable detections for any illegitimate usage of the SoftPerfect Network Scanner (netscan.exe).
- Routinely audit administrative user account groups for anomalous entries.
- Ensure monitoring is enabled to detect malicious use of:
- Task Manager (taskmgr.exe), or child processes of Task Manager, to create dump files of LSASS (lsass.dmp) in the TEMP folder.
- Ntdsutil (Ntdsutil.exe) to create copies of NTDS.dit
- Block the execution of Ntdsutil for accounts where it is not needed.
- Implement allow lists of authorized RMM services. Alternatively, monitor for, or block the execution of unauthorized RMM services.
- Enforce a password policy requiring strong passwords to prevent brute force attacks.
- Enforce MFA on all user accounts.
Implement network segmentation wherever possible to limit a threat actor’s ability to spread through networks after gaining initial access.