Threat Report: alberta.ca Spoofed in Targeting Education Sector
TLP:CLEAR
Source: Closed Source | Reported to CyberAlberta
Overview:
CyberAlberta recently became aware of targeted malicious emails being delivered to multiple organizations in Alberta's education sector. These malicious emails impersonate the Government of Alberta by using official branding and spoofing the sender display name to appear as though they originate from a @alberta.ca address.
Spoofing refers to a technique used by malicious actors to manipulate email headers, such as the sender address, to make the email appear as if it originated from a trusted source.
- All malicious emails observed so far have the sender display name set to admin@alberta[.]ca, but the sender domain in all cases has been holyfamilyaston[.]org. The sender claims to be from the "2025 Government of Alberta Information Verification", urging the recipient follows a link to verify that the information in the email is accurate and current.
- The sender of the email attempts to apply pressure on the target by claiming the link expires in 24 hours, warning them that failing to verify the information within this time frame will result in the revocation of a license.
- The data the recipient is requested to verify is gathered from publicly available information about the target organization, likely to further give the impression of being a trusted sender.
- The observed malicious links contained in the emails have been crafted by the threat actor using the legitimate Pantheon.io web hosting service. In doing so, the threat actor can create custom Alberta-themed links to further give the appearance of legitimacy.
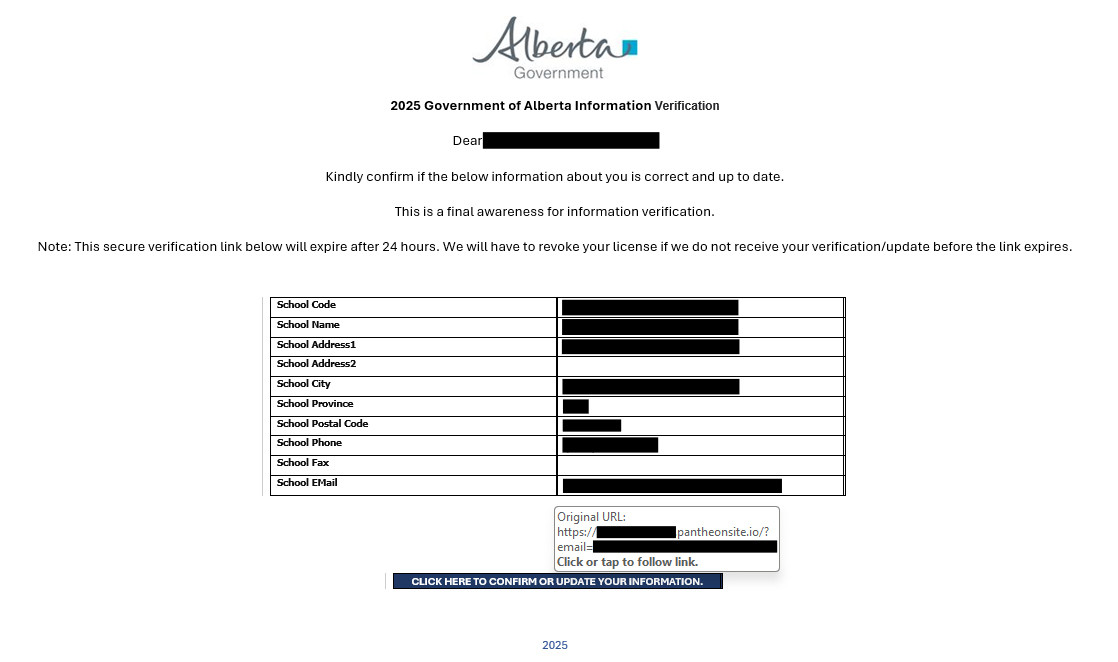
Figure 1 - Example of malicious email impersonating the Government of Alberta.
The malicious links in the emails redirect recipients to a web page impersonating the Government of Alberta designed to harvest credentials. Submitting credentials could result in malicious actors gaining access to the target organization's environment, facilitating further attacks such as ransomware.
What to Communicate to Executives:
- Maintain Vigilance: Raise awareness within your organization to this ongoing threat. Do not interact with any links contained in similar targeted emails. And report the email to your relevant teams.
- Emails Delivered to Executives: In all observed cases, the malicious emails have been sent to executives and heads of departments, likely due to these personalities often having publicly available contact information.
- Prevent Domain Spoofing: If your organization has the capability to do so, and if not done so already, ensure that DMARC, along with SPF and DKIM, is enabled to prevent your organization's domain name from being spoofed.
- Potential for Expansion: While this campaign appears to currently be targeting the education sector, there may be other similar emails targeting other sectors within Alberta.
Report to CyberAlberta: If any organization receives a similar malicious email, please report to CyberAlberta. Increased visibility on these incidents can lead to a better understanding of the threat, and better defences.
Further Reading: