Spear Phishing Campaign Targets Alberta’s Insurance Industry
TLP:CLEAR
Source: CyberAlberta Investigation
Overview
Since May 2nd, an unknown threat actor targeted multiple organizations in Alberta’s insurance industry with highly targeted phishing emails. These emails impersonated the Government of Alberta, specifically the Office of the Alberta Superintendent of Insurance, in an effort to initiate contact with recipients. While the full intent of these attacks remains unclear, the phishing message (pictured below in Figure 1) is likely an attempt at initial contact designed to build trust with targets. Any subsequent engagement could facilitate the delivery of a malicious payload intended to exfiltrate sensitive data or establish a foothold within the target’s environment, potentially enabling high-impact follow-on attacks such as ransomware deployment.
The email attempts to create a sense of urgency through a concerning subject line: “RE: Code Violation Notice | #002746”. The body of the message reinforces this pressure by alleging that the Chief Administrative Officer, named by the threat actor as Lalonnie Cheung, has previously attempted to make contact and is now following up. This framing is designed to imply that the recipient is responsible for a delay in addressing an urgent matter, thereby inducing panic and prompting a hasty response.
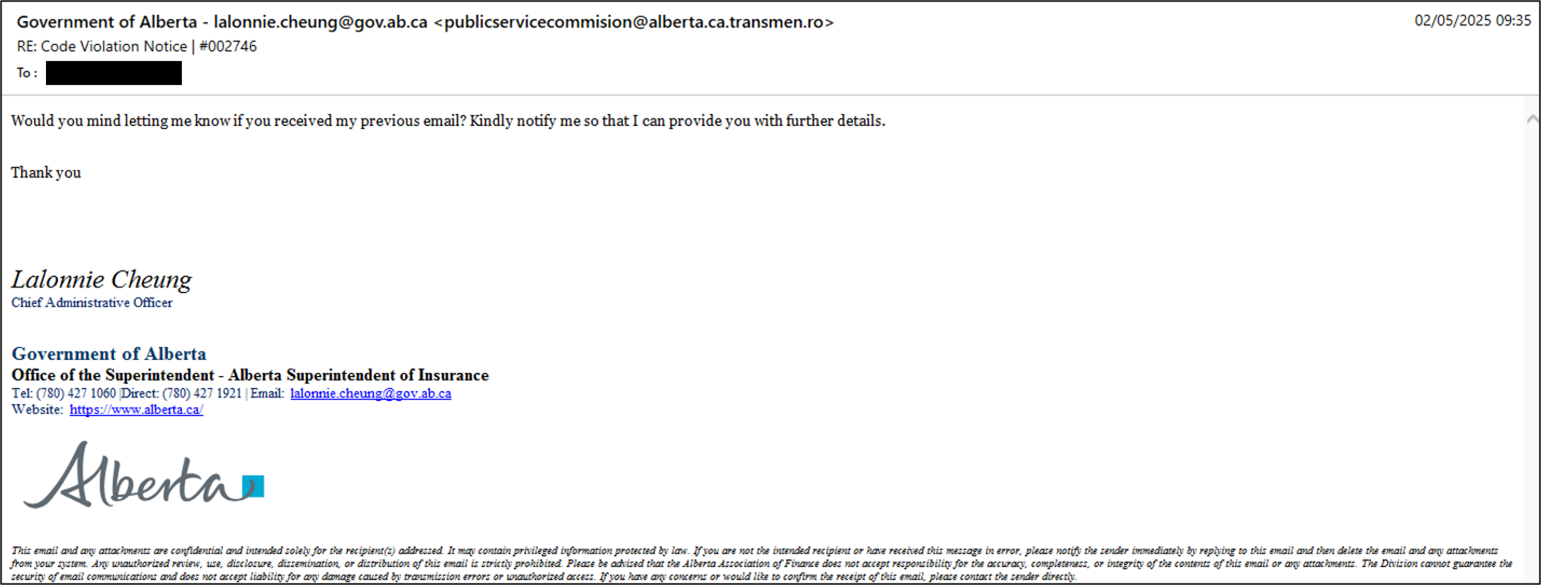
Figure 1 - Sample of the phishing email targeting Alberta's insurance industry.
Recipients of this email are strongly advised not to engage with the sender. If any communication has already occurred, it should be discontinued immediately, and the incident should be reported to your security or IT team for further investigation and assessment of potential exposure. Refer to the Recommendations section at the end of this report for guidance on mitigating risks associated with email spoofing.
Technical Analysis
Reconnaissance
The threat actor appears to have conducted reconnaissance using publicly available information to compile a targeted list of victim organizations, all operating within Alberta’s insurance sector. As part of this effort, the actor identified the Office of the Alberta Superintendent of Insurance as a credible authority figure to impersonate, likely to enhance the perceived legitimacy and urgency of the phishing emails. The messages included the Government of Alberta’s official logo and publicly available legitimate government contact numbers, increasing the appearance of authenticity to the messages.
The primary indicator undermining the email’s impersonation is the use of the name and title “Lalonnie Cheung, Chief Administrative Officer.” According to the Office of the Alberta Superintendent of Insurance, no individual by that name or position currently works in the department.
Resource Development
Analysis of the phishing email headers indicates that the threat actor employed a dual strategy to maximize the likelihood of successful delivery. The threat actor used Google Workspace services in combination with a weak DMARC policy on the spoofed sender domain (transmen[.]ro), increasing the likelihood of the message bypassing security filters.
Authentication results show that the email passed DKIM validation, likely due to the threat actor registering and configuring the malicious subdomain impersonating the Government of Alberta (alberta.ca.transmen[.]ro) within Google Workspace. This gave the message a legitimate Google signature, increasing the chances of evading detection.
dkim=pass header.d=alberta-ca-transmen-ro.20230601.gappssmtp.com
Figure 2 - The phishing email's DKIM header.d value.
The DKIM header provides insight into the threat actor’s infrastructure. The presence of gappssmtp.com suggests that DKIM signing was enabled through Google Workspace. Notably, the header prefix aligns closely with the spoofed sender address used in the phishing email (alberta.ca.transmen[.]ro), indicating a deliberate attempt to craft a domain that appears related to the Government of Alberta. The domain transmen[.]ro is registered to a legitimate Romanian transport company, Trans Men 86 SRL. Open-source scanning of the domain revealed a publicly accessible login page for the site's management platform cPanel, suggesting possible misconfiguration or exposure of administrative services.

Figure 3 - Screenshot of cpanel.transmen[.]ro
These findings raise the credible possibility that the transmen[.]ro domain, specifically its cPanel instance, may have been compromised. Such access would allow the threat actor to easily create temporary subdomains such as alberta.ca.transmen[.]ro, for the purpose of launching highly targeted spear phishing campaigns under the guise of a legitimate infrastructure.
Defence Evasion
Another likely reason for the use of the transmen[.]ro domain as the sender address is its misconfigured DMARC policy permitting email spoofing.
v=DMARC1; p=none;
Figure 4 - DMARC policy for transmen[.]ro
With the policy (p) set to none, attackers are able to spoof the transmen[.]ro domain without restriction, as this setting instructs recipient mail servers to take no specific action on authentication failures. Additionally, the absence of a DMARC subdomain policy (sp tag) means there are also no controls preventing the use of arbitrary subdomains, such as alberta.ca.transmen[.]ro, for the same purpose.
Conclusion
The presence of potentially vulnerable public-facing applications, misconfigured or weak email authentication policies, and the use of Google Workspace collectively provide a plausible explanation for how these phishing emails were able to pass DKIM validation and successfully reach the inboxes of numerous organizations across Alberta’s insurance industry, generating significant concern among recipients.
Much like the widespread phishing campaign that targeted Alberta’s education sector in January, this latest incident underscores the lengths to which threat actors will go to craft convincing phishing lures. It highlights the ongoing need for heightened user awareness, robust email filtering, and careful scrutiny of any unsolicited or unexpected messages.
Recommendations
- Organizations in the insurance industry are advised to scan their email environments for any messages originating from the transmen[.]ro domain and assess for potential indicators of compromise or follow-on activity.
- If any suspicious behavior is identified and investigative support is required, please report to CyberAlberta’s Threat Intelligence team.
- All members are encouraged to implement detection and response mechanisms that flag discrepancies between the DKIM-signed domain and the visible "From" address. Additionally, exercise caution when receiving unexpected messages that attempt to create a sense of urgency or pressure immediate action.
- Ensure all public facing applications are fully patched, and enforce a strong password policy in combination with multi-factor authentication (MFA) to prevent asset compromise and their potential use as infrastructure in future attacks.
Indicators of Compromise
Network Indicators
| Indicator Type | Value |
| Email Sender Domain | publicservicecommision[at]alberta.ca.transmen[.]ro |
| Email Sender Display Name | Government of Alberta – lalonnie.cheung[at]gov.ab[.]ca |
| Email Subject | RE: Code Violation Notice | #002746 |
| DKIM header.d | alberta-ca-transmen-ro[.]20230601.gappssmtp[.]com |