Spotting the Signs: Staying Ahead of Cyber Threats
In today’s rapidly evolving digital landscape, the ability to identify and respond to cyber threats is more critical than ever. As attack methods grow more sophisticated and frequent, driven by advances in Artificial Intelligence (AI), increased cloud adoption, and persistent social engineering tactics, organizations must rely on technical defenses and informed vigilance to stay ahead of threat actors. Understanding the patterns behind these threats is essential for building resilient systems and empowering teams to detect and act on early warning signs.
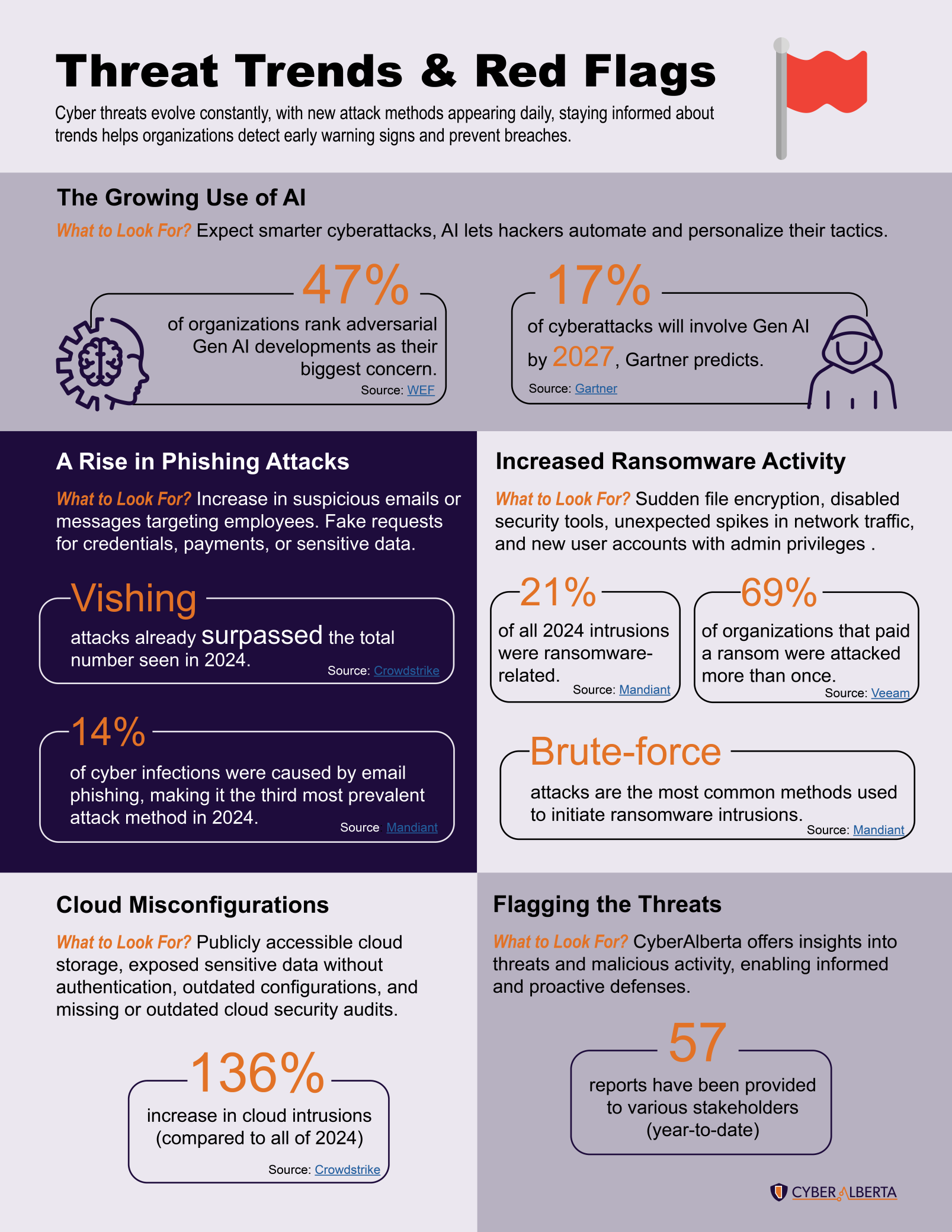
AI-Powered Threats on the Rise
AI is no longer just a tool for defenders; it’s being weaponized by attackers. With 47% of organizations citing adversarial Gen AI as their top concern, and Gartner predicting 17% of cyberattacks will involve Gen AI by 2027, the need to monitor AI-driven tactics is urgent. These attacks are smarter, faster, and more personalized, making early detection more challenging than ever.
Ransomware is a Persistent Menace
Ransomware continues to dominate the threat landscape. In 2024, 21% of all intrusions Mandiant responded to were ransomware-related, and 69% of organizations that paid a ransom were attacked again. Brute-force attacks remain the most common entry point, often targeting weak credentials and remote access points. The main methods of brute-force attacks being password spraying, the exploitation of default credentials on VPN devices, and remote desktop protocol (RDP) login attempts.
Phishing Evolves and Expands
Phishing remains a top threat vector, with email-based attacks responsible for 14% of cyber infections in 2024. Alarmingly, vishing attacks have already surpassed last year’s totals, signaling a shift toward more direct and deceptive tactics. Organizations should be on high alert for suspicious communications, including fake requests for credentials, financial transfers, or sensitive data, often disguised as urgent or familiar messages targeting employees.
Cloud Misconfigurations are a Silent Risk
With a 136% increase in cloud intrusions in the first half of 2025, misconfigured cloud environments are a growing concern. Publicly accessible storage, exposed data, outdated settings, and missing audits are all red flags that can lead to serious breaches.
Recognizing the Red Flags: CyberAlberta’s Role in Proactive Cyber Defense
CyberAlberta plays a role in helping organizations identify and respond to emerging threats. In 2025 alone, we’ve delivered 57 intelligence reports to stakeholders, equipping decision-makers with timely insights to strengthen their cyber defenses. These reports support a shift from reactive security to proactive resilience.
Cyber threats don’t wait, and neither should we. By recognizing the red flags and leveraging trusted intelligence sources, organizations can better protect their data, systems, and people.
Sources: